Google Artifact Registry
This tutorial will guide you on how to create a private registry in Google Artifact Registry, its necessary credentials, and how to use it in Okteto.
The steps to do it are:
- Create Service Account with Artifact Registry access
- Get Service Account Credentials
- Okteto config with credentials
Step 1: Create Service Account with Artifact Registry access
To have access to Artifact Private Registry in Google Cloud you need to use a Service Account. As tokens generated by GCP are temporary, and do not provide a username/password.
Create Service Account with Role
You can create it using the gcloud cli (Command Reference) or with the Console, in the IAM & Admin API section.
Using the command reference:
gcloud iam service-accounts create {SA_NAME} \
--display-name="My Service Account"
gcloud projects add-iam-policy-binding {PROJECT_ID} \
--member=serviceAccount:{SA_NAME}@{PROJECT_ID}.iam.gserviceaccount.com \
--role=roles/artifactregistry.reader
In the Console:
- Click on Service Accounts option in the left side menu
- Create Service Account
- Add Role with GCR Read Role
- Artifact Registry Reader
- DONE
Step 2: Get Service Account credentials
Now we need to create Access Key to use this credentials.
Using the command reference:
gcloud iam service-accounts keys create SA_KEY_FILE.json \
--iam-account=SA_NAME@PROJECT_ID.iam.gserviceaccount.com
This will create a file with the ServiceAccount Key as well.
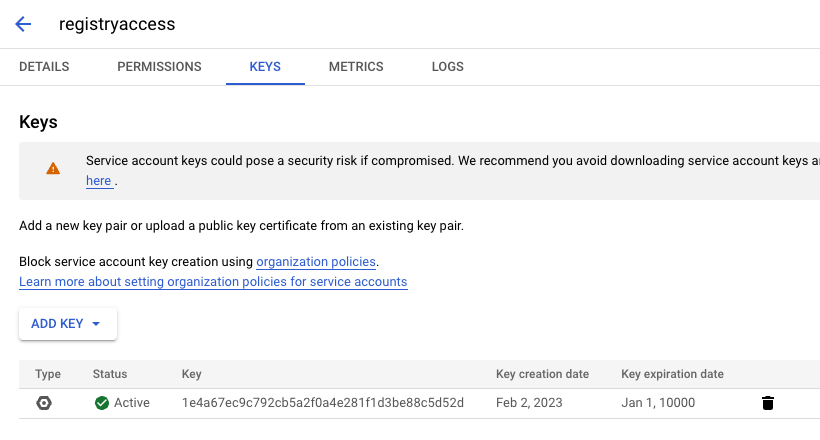
In the Console:
- Navigate to IAM & Admin → Service Accounts
- Open your Service Account → KEYS tab
- Create new JSON key and store it → sa_key.json
Step 3: Okteto Config with Credentials
Add your credentials to the admin dashboard following these instructions after signing into your Okteto instance.
Example:
Host: europe-west1-docker.pkg.devUser: _json_keyPassword: sa_key.json
Or you can use _json_key_base64 as user and Encode your Service Account Key file (cat sa_key.json | base64).