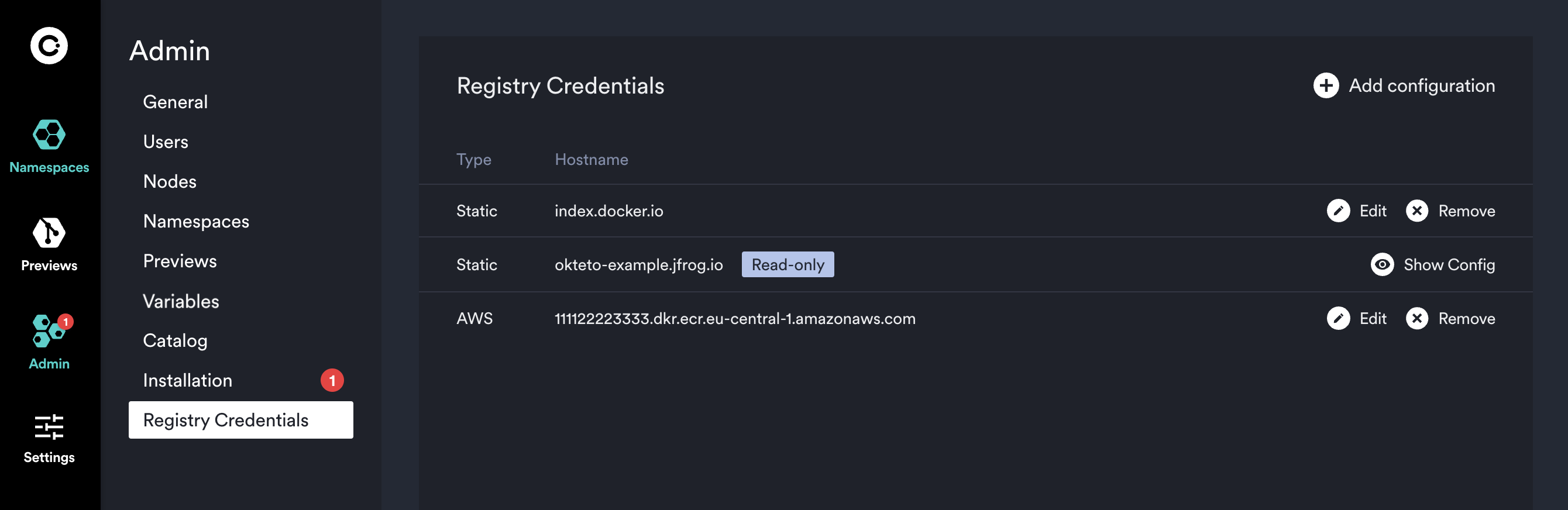
Registry Credentials
In the Admin Dashboard, you can set up private registry credentials for your Okteto instance. These credentials are automatically used by Okteto for various developer operations like building and deploying, so developers don't need direct credential access. Once set, all developers can access the registries through Okteto without additional steps. Additionally, you have the option to manage these credentials via Kubernetes CRDs provided by Okteto.
When the daemonset.configurePrivateRegistriesInNodes.enabled setting is active, Okteto automatically applies registry credentials to nodes, allowing cluster-wide access to these registries.
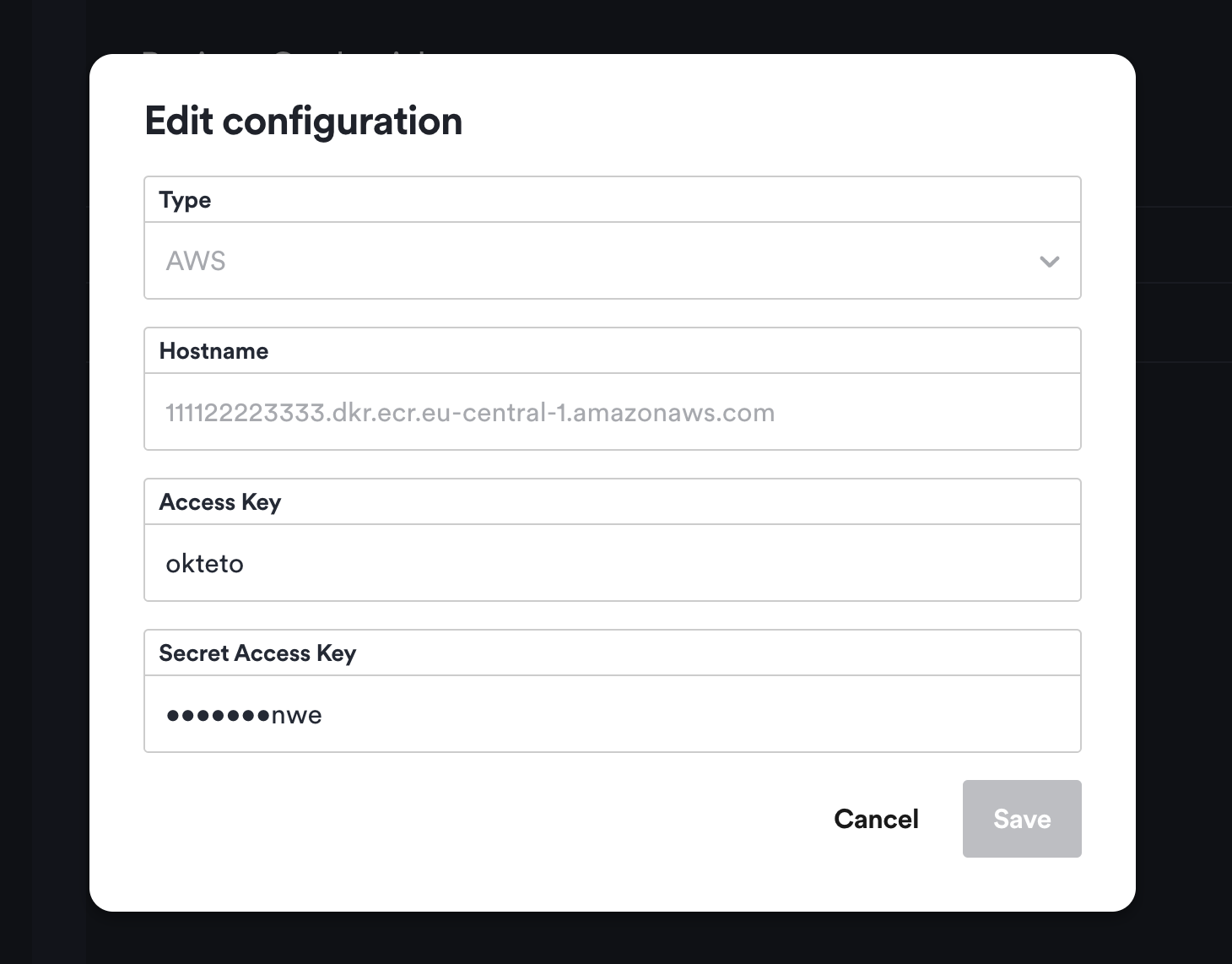
Registries are listed by type (Static or AWS) and hostname. Static credentials use a username and password, ideal for platforms like Docker Hub. AWS credentials for ECR use an Access Key and Secret, with Okteto refreshing credentials every 4 hours. For AWS, ensure the registry hostname ends with .amazonaws.com. Instructions are provided for retrieving ECR credentials.
Follow one of the guides below to learn how to retrieve your registry credentials:
Registries must be included using a valid host name. For example, index.docker.io or 111122223333.dkr.ecr.eu-central-1.amazonaws.com. For static registries, if the registry is exposed in a port other than the default http(s) 80/443 it must be included in the name, eg: my-registry.com:5000
This admin view also enables you to rotate your registry credentials or delete them if you don't need them anymore. For sensitive data you will only see the last few characters as a hint to verify the value.
Be aware that any changes you make to credentials may take a few minutes to propagate to all of the components in the cluster.